Companies with Alleged Ties to Chinese Government Under US Government Scrutiny

By Anne-Liese Heinichen
In October of 2018, Bloomberg published a report entitled “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies” that described how nearly 30 American companies stored data on servers that contained chips which had allegedly been secretly inserted during the manufacturing process in China by members of the People’s Liberation Army. Among the allegedly affected companies were Apple, a large unnamed banking institution, Department of Defense contractors and Amazon, who the report states, discovered an intrusion while performing a security audit on video compression servers that had been assembled by Super Micro Computer Inc. during a build of a secure cloud for the CIA.
Bloomberg further claims that US Government intelligence agencies were made aware of a threat in 2014 of the Chinese military attempting to insert chips into Supermicro motherboards; however, “it wasn’t clear from the intelligence whom the operation was targeting or what its ultimate aims were” and that “a broad warning to Supermicro’s customers could have crippled the company, a major American hardware maker”.
1 With corporate revenues exceeding over $2 billion
2, Super Micro Computers, commonly referred to as Supermicro, is the dominant source for motherboards in the US, nearly all of which are manufactured by Chinese contractors, according to Bloomberg.
Microchips such as these can allow hackers to secretly access any network which contains these tampered servers, an intrusion potentially providing unlimited and undetected access. These microchips allegedly were colored gray or off-white and resembled signal conditioning couplers as opposed to microchips and varied in size depending on the motherboard model. According to Bloomberg’s sources, the microchips were designed to enable the editing of information through the insertion of code or altering the information of operating system data as it was being stored in the motherboard’s temporary memory and then directed to the CPU. This enabled the device to communicate with computers elsewhere on the Internet and prepared the device to receive new code from these external sources allowing hackers to change how the device functioned.
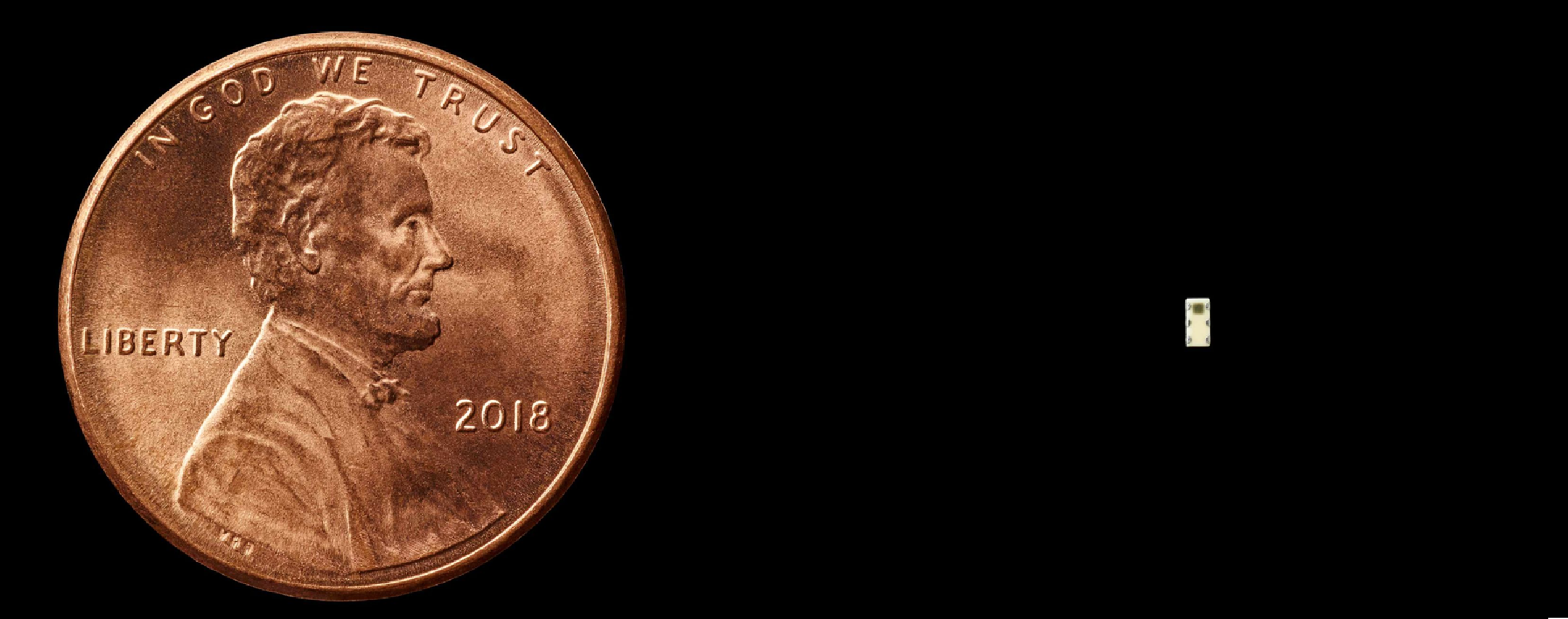
According to Bloomberg, government investigators were able to review documentation for the hardware and allegedly traced the malicious chips to four Chinese subcontracting manufacturers. The infiltrators were individuals claiming to work for Supermicro or who claimed connections to the Chinese government who then requested changes to the motherboards’ designs and offered bribes or used the threat of inspections and shut downs to the subcontracting factories. The investigators concluded this plan was designed by a People’s Liberation Army unit specializing in hardware attacks.
3 To date, the Bloomberg article states that there is, “no commercially viable way to detect attacks like the one on Supermicro’s motherboards…or has looked likely to emerge”.
Apple, Amazon and Supermicro have denied the claims made by Bloomberg. Bloomberg maintains it has 17 confidential sources, including US Government officials, that can confirm the intrusion but has not provided evidence to substantiate their claim. Apple has since ended its relationship with Supermicro. The day the story was published by Bloomberg, Supermicro’s share price took a nosedive from $21.40 to $12.60 and, as of December 31, was priced at $13.80 a share.
For years U.S. Government officials have expressed concerns over the Chinese government’s involvement with Chinese manufacturers such as Huawei and ZTE. In October of 2012, a US House Intelligence Committee report implied that Huawei and ZTE posed a national security threat as they believed the companies were conducting cyber espionage on behalf of the Chinese government. The report recommended blocking acquisition attempts involving both companies, not using either company’s equipment in sensitive government systems and discouraged the use of either company’s products by the commercial sector.
In March of 2017, ZTE pleaded guilty to the violation of US trade sanctions through the illegal export of American technology to Iran and North Korea and was fined $1.19 billion. Subsequently, in April 2018 the US Department of Commerce banned American companies from providing exports to ZTE. In May, ZTE announced the suspension of most manufacturing activity. In July, the Department of Commerce lifted its ban.
Huawei has similarly faced accusations of violation of intellectual property rights and cyberespionage. From accusations made by a former National Security Agency director to documents leaked by Edward Snowden, Huawei, whose founder, Ren Zhengfei, served as an engineer in the Chinese People’s Liberation Army, has been suspected of having strong ties to the Chinese government. In April 2018, the US Justice Department reportedly joined an investigation into possible violations of economic sanctions made by Huawei through the supply of its equipment to Iran, Venezuela, North Korea and Syria. In December 2018, Ren Zhengfei’s daughter and Huawei CFO, Meng Wanzhou, was arrested in Canada at the behest of US authorities. Wanzhou has been charged with conspiracy to defraud multiple international institutions by representing to US banks that Huawei and a company alleged to have done business with Iran called Skycom were separate entities though the government alleges that both companies are one and the same. As of the date of this article, Wanzhou remains under house arrest in Vancouver.
On November 1, the US Justice Department announced a federal grand jury indictment against a state-controlled Chinese company, its Taiwanese partner company and three individuals for “conspiracy to steal, convey and possess stolen trade secrets of an American semiconductor company for the benefit of a company controlled by the PRC government.”
4 The named defendants are: United Microelectronics Corporation (UMC), Fujian Jinhua Integrated Circuit, Co., Ltd, Chen Zhengkun aka Stephen Chen, He Jianting aka J.T. Ho; and Wang Yungming aka Kenny Wang.
|
"As this and other recent cases have shown, Chinese economic espionage against the United States has been increasing—and it has been increasing rapidly. I am here to say that enough is enough. With integrity and professionalism, the Department of Justice will aggressively prosecute such illegal activity.”
Attorney General Jeff Sessions
|
According to the indictment, the Chinese government has designated the development of DRAM technology as a national economic priority. Fujian Jinhua Integrated Circuit (hereafter referred to as Jinhua) was established in 2016 by PRC funding with the goal of “designing, developing, and manufacturing DRAM”.
5 Chen Zhengkun was employed by UMC in September 2015. The complaint alleges that Jinhua and UMC conspired to illegally obtain Micron Technology’s proprietary DRAM technology by having Chen recruit and hire Micron Memory employees, including Ho and Wang, to join him at UMC after downloading confidential Micron files from October 2015 through April 2016. UMC then provided the technology relating to the design and manufacture of DRAM to Jinhua. The stolen data included wafer specifications for Micron’s 25nm DRAM chip as well as Micron’s F32nm design. The complaint states that from September 2016 through March 2017, UMC and Jinhua filed five patents and a patent application containing information that was the same or very similar to technology described in Micron’s Trade Secrets that allegedly could not be obtained through reverse engineering. Chen became the President of Jinhua in charge of its DRAM production facility in February 2017 in addition to his position at UMC. Prior to the allegations set forth in the complaint, UMC did not manufacture or possess advanced DRAM technology. Micron estimates the value of the eight trade secrets to UMC and Jinhua was at least $400 million and up to $8.75 billion.
If convicted, Chen, Ho and Wang each face 15 years’ imprisonment and a $5 million fine for economic espionage charges and 10 years’ imprisonment for theft of trade secret. UMC and Jinhua face forfeiture and a maximum fine of $20 billion.
The Justice Department has also filed a civil lawsuit seeking to block UMC and Jinhua from transferring the stolen technology or exporting products based on the stolen technology to the US. In October 2018, the US Department of Commerce restricted US companies from selling components, software and technology goods to Fujian Jinhua.
In November 2018, China responded to allegations that its government-backed firms are stealing American technology by declaring that US moves, including the Section 301 tariffs, violate World Trade Organization rules and only seek to protect the US’ monopoly on the DRAM industry.
As the above examples illustrate, cybersecurity is a problem everywhere and for everyone: threats continue to increase globally and not just individual organizations are at risk but also entire nations. It is the responsibility of each link in the global supply chain to ensure their organization is proactive in their cybersecurity efforts for the benefit of the overall economy.
1 https://www.bloomberg.com/news/features/2018-10-04/the-big -hack-how-china-used-a -tiny-chip-to-infiltrate -america...
2 https://www.supermicro.com/about/index.cfm
3 https://www.bloomberg.com/news/features/2018-10-04/ the-big-hack-how -china-used-a-tiny-chip-to-infiltrate -america-s...
4 https://www.justice.gov/opa/pr/prc- state-owned-company -taiwan-company-and-three-individuals -charged-economic-...
5 United States of America v. United Microelectronics Corporation; Fujian Jinhua Integrated Circuit, Co., Ltd.; and Chen Zhengkun aka Stephen Chen Complaint filed 11/1/2018.