Cyber Crime, Your Bank Accounts, and Your Insurance

Kristal Snider, ERAI
Nearly half of all business owners carry some form of cyber insurance but small businesses lag behind, largely because they don’t see themselves as vulnerable to an attack when, in fact, they are viewed by cybercriminals as the lowest hanging fruit. Rightfully so considering a startling 47% of small to midsize companies have not made cybersecurity a priority.
While government agencies, financial institutions, and the healthcare sector are becoming increasingly regulated, smaller, unregulated companies have emerged as an “ideal target” and a potential backdoor entrance to larger companies. According to a report released by BakerHostetler, 37% of the cyber breaches they investigated were directly related to employee negligence despite evidence that employee training can reduce the risk of a cyber related incident by 45 to 70 percent.
According to Howard Miller, Director of the Tech Secure® Division of LBW Insurance, the global cyber threat landscape can be broken down into two key areas:
1.) The cybercriminal is stealing from you. This is typically done by opening a malicious attachment, link, or website resulting in harmful code infecting your network. Banking credentials or banking Trojan software can then be used to steal money out of your account or fraudulent or altered instructions directed at the bank, purporting to be from you, result in funds being fraudulently transferred.
2.) You unwittingly transfer money to the cybercriminal. This type of cybercrime has been dubbed Business Email Compromise (BEC), CEO fraud or social engineering. According to the FBI, these sophisticated scams, targeting businesses working with foreign suppliers and businesses that regularly perform wire transfer payments, are increasing exponentially. This deception causes the business to transfer money to the cybercriminal under various tricks of confidence. In other words, the victim is sending money to what they believe to be a legitimate entity, but then find out that it’s a criminal purporting to be a legitimate entity or individual.
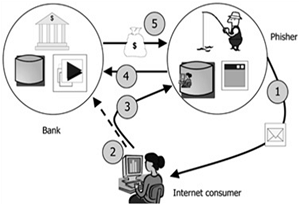 Don’t Become a Cybercrime Statistic
Don’t Become a Cybercrime Statistic
A recent example of a business giving money to cybercriminals was reported by ERAI on September 16, 2016. A buyer located in the Czech Republic placed numerous purchase orders with a supplier in Hong Kong for goods totaling $43,152.72. Despite the fact payment was not received by the supplier within 10 days of delivery as agreed, alarm bells were not set off because the two organizations had enjoyed a successful business relationship since 2014 and both had been engaged in the purchase and sale of electronic components since the mid-90s. Unbeknownst to either party, the cybercriminals were intercepting and reviewing email communications while patiently waiting for just the right time to intervene.
The buyer never noticed when the last two characters of the supplier’s email changed from “hk” to “tk” and did not question instructions for payments to be made to two new bank accounts. It wasn’t until the supplier began requesting payment for the now delinquent invoices that the fraud was exposed. The buyer had paid all of the invoices, within the agreed upon payment terms, to bank accounts belonging to cybercriminals that have since been closed. The thieves were long gone.
The buyer argues they paid for the goods and they should not be forced to pay for them a second time and feels strongly the supplier should be held responsible since they continued to ship product despite not receiving payment as agreed.
The supplier, out the goods and the money, argues the buyer should have called to verify the change in wire instructions before sending funds to a third party account that did not even bear their company’s name.
I’ve asked James Melendres (JM), Partner and Co-Chair of the Cybersecurity, Data Protection, and Privacy practice of Snell & Wilmer, Howard Miller (HM), Director of the Tech Secure® Division of LBW Insurance and Petra Stuhmeier Griffith (PG), SVP Director of Product Development for Grandpoint Bank, to weigh in on a few of the more commonly asked questions posed by victims of these types of scams and to offer recommendations and solutions business owners can deploy to reduce these risks.
KS: James, both the buyer and the supplier were victimized, so who is right, who is wrong and who is ultimately liable? Is the Buyer obligated to pay the supplier even though they already wired payment in full to the cyber thieves?
JM: That’s a good question and not one that is easy to answer. Unless it has been specifically spelled out in contract terms, purchase orders, or invoices, liability for losses resulting from BEC fraud will likely only be determined through protracted litigation. These cases typically involve arguments about the applicability of broader contractual clauses and theories of tort liability. Because this is such a new risk, there is very little case law litigants and judges can draw upon, which causes uncertainty and unpredictability for both suppliers and buyers who find themselves victimized by sophisticated cybercriminals.
KS: Is determining liability contingent upon whose email server was compromised or is responsibility going to rest primarily with the sender of the funds?
JM: Again, and unfortunately, there is no straightforward answer. There is likely liability on the part of both the buyer and the supplier. The party whose email server was compromised may be liable to the extent that it did not implement cybersecurity best practices, such as regular network penetration testing, multi-factor authentication and verification, limitations on administrative access, and network segmentation, especially if it is determined that these failures resulted in the network intrusion that allowed the cybercriminal to modify the email address. Liability based on this type of poor cyber hygiene will be heightened if the contract required these practices. On the other hand, the sender of funds may also face liability for failing to confirm the change in wire instructions. The fact that the cybercriminal’s attack may generate a civil lawsuit between two victims only adds insult to injury.
KS: In the case cited above, the buyer is in the Czech Republic, the supplier is in Hong Kong and the cybercriminal’s bank account was in Malaysia creating a multi-jurisdictional quagmire. What legal remedies do American business owners have if they find themselves victims of this scam knowing the other parties will most likely be outside of the U.S.?
JM: As long as there is a jurisdictional nexus to the United States, American business owners will always be able to file a lawsuit against the cybercriminal. However, the reality is that serving process on a foreign hacker, much less enforcing a judgement, is extremely difficult as a practical matter. On the criminal justice side, although the Department of Justice and Federal Bureau of Investigation regularly investigate and charge cybercriminals located overseas, extraditing those individuals to the United States remains a significant challenge and can take years to accomplish.
KS: Are there any terms or conditions organizations should include in their purchase order or invoice that would help reinforce the responsibility of one party over the other in the event of a loss such as this?
JM: Certainly. As I’ve alluded to in my previous answers, a lack of clearly defined contractual terms will likely result in litigation between the buyer and supplier following a BEC attack. By contrast, if parties agree to terms about cybersecurity standards as well as standard business terms, like verifying any change in wire instruction, liability will be more clearly defined in the aftermath of this type of crime. Companies can further reduce their risk of falling subject to a BEC attack by updating their information security policies and instituting regularly employee training that highlights these types of risks.
KS: What about the bank? Does the financial institution have any liability or responsibility?
JM: In general, the answer is no, although every case is different and should be analyzed by legal counsel. In the circumstance described above, the bank simply executed a wire transfer order that the buyer voluntarily provided, so it unlikely to be held liable.
PG: Always check with legal counsel and your financial institution regarding this subject. But for Business Email Compromise fraud cases, the financial institution is typically not liable.
In the US, wire transfers are governed by Uniform Commercial Code. Banks typically have agreements with customers to implement security procedures to protect against fraud, such as wire passwords, dual control and secondary authentication/verification. As long as the bank can prove that its security procedures are commercially reasonable in providing security against unauthorized payment orders and the bank proves that it accepted the payment order in good faith and in compliance with the security procedure, the liability will fall on the customer.
With Business Email Compromise, the customer believes it is sending the payment to a legitimate entity and initiates and approves the payment transfer. Even if the bank were to flag the payment and call the client to confirm that they wanted to submit the payment, the client would likely confirm the payment because they don’t suspect that there’s anything wrong. In most cases, the bank has held up its end of the agreement and is not liable.
Some people believe that the FDIC insurance may be liable or cover some of these losses, but FDIC insurance only protects accounts if your insured banking institution fails. FDIC deposit insurance also does not protect accounts from fraud or theft online (or otherwise).
KS: Given this information and assuming the financial institution has the proper security measures in place, it sounds like businesses should prepare to take responsibility for their own losses.
PG: That’s the exact point. For Business Email Compromise, it is the failure of the business customer’s security and not the bank’s security. Banks are heavily regulated and have really beefed up their security infrastructure in recent years due to regulatory pressures. Small to medium sized companies are much easier targets than banks, so cyber criminals are now targeting these businesses instead of the banks directly.
KS: Howard, now that we know the bank is likely not liable for the loss, who is ultimately responsible for filing an insurance claim?
HM: Coverage for loss due to deception is focused on an act committed by a person falsely purporting to be a vendor, client, or employee of the business customer which results in the transfer, payment, or delivery of money and not other property such as inventory. There is no obligation to file a claim but companies with appropriate insurance could have a financial backstop where many others would have to incur the total loss.
KS: So let’s assume a U.S. supplier ships product to an international customer and that the customer wires payment(s) to a cybercriminal instead of the supplier. The customer has no cyber insurance and they are not willing or are not financially able to pay for the goods a second time. The supplier is out the money they are owed and their inventory. Is there an insurance solution that would protect a supplier in this situation?
HM: A safe answer would be no but there is an area outside of this article for accounts receivable insurance.
KS: From an insurance claims standpoint, what’s the proper protocol for responding to this type of loss?
HM: From an insurance claims standpoint, these are the guidelines I recommend:
- Notify the financial institution. They have relationships with law enforcement that can assist in getting funds back if possible.
-
Notify your insurance provider as there may be time reporting requirements.
-
If the loss involves a violation of law, you must notify local law enforcement authorities and file an Internet Crime Complaint (see www.ic3.gov for more details).
-
Keep all pertinent documents and records which can verify the amount of any loss. Cooperate in the investigation and settlement of any claim.
KS: I wrote another article for this edition of INSIGHT titled, “Cyber Crime Victim Sues Insurance Provider for Denying $480,000.00 Claim” where I talked about a Texas manufacturer by the name of AFGlobal that is suing its cyber insurance provider for refusing to cover a BEC claim similar to the one I just shared. AFGlobal maintains that the policy it held provided coverage for both computer fraud and funds transfer fraud, but the insurer is arguing that email fraud does not meet the definition of “computer fraud” covered by AFGlobal’s policy. Isn’t the whole point of cyber insurance to protect against this type of fraudulent activity?
HM: Cyber liability are good insurance policies but deserve a separate article. They are focused on confidential data or network operations affected by a virus, hack or denial of service attack and can be very limited in their coverage for monetary losses described here. Under a standard commercial crime insurance policy, this type of loss may not be covered as theft, even though the result is the same – loss of money due to a cybercriminal. Insurance is a puzzle and it’s about putting together the right pieces. There is a difference between buying an insurance policy and knowing what’s not covered. I find when I act as a consultant for my clients it also allows me to customize their insurance based on risk analysis.
Why AFGlobal’s policy did not respond goes back to my comments about the business transferring money to the criminal voluntarily. In the latter part of 2014, the insurance industry responded to this risk. This year from the April 2016 FBI Phoenix division report on BEC to the June report, the number of worldwide victims increased by about 25% and exposed damages are up about 34% from $2.3 billion to $3.1 billion. An individual physical bank robbery usually nets under $10,000. An average business email compromise can be around $130,000. Many criminals are overseas, insulated from direct physical threat and make it difficult for US law enforcement to prosecute them. It was clear to me that as losses continue to increase, neither the financial institutions, nor the customers can shoulder the entire cost of cybercrime.
KS: I expect more businesses like AFGlobal are going to find out the hard way about the gaps that exist in their cyber insurance policies that could leave them completely exposed to scams like BEC. If these types of scenarios aren’t covered in a cyber security policy, what can business owners do protect themselves?
HM: In early 2015 I started working in partnership with Grandpoint Bank to develop a group insurance product for business banking customers to provide affordable and targeted protection against cybercrime. The bank had started seeing its customers fall victim to Business Email Compromise scams and, while they were able to recover most of the losses, they wanted to provide their customers a way to protect themselves from these kinds of losses. The idea was to fill the gap that most insureds may not realize even exist in their current insurance program. The result was an insurance policy that can enhance a company’s existing insurance or fill the gap. It’s offered at a price point that most businesses can justify while protecting one of their most valuable assets, their bank accounts. It is designed to cover fraudulent transfers as well as cyber deception.
The Client Cyber Crime Insurance policy is available exclusively to business clients of Grandpoint Bank and its divisions, Bank of Tucson, Regents Bank and The Biltmore Bank of Arizona, through Grandpoint Insurance Services, in partnership with LBW Insurance & Financial Services, Inc.
KS: Petra, why offer this program to your customers?
PG: Educating and alerting our clients, and the broader business community, about established and emerging cybercrime trends is a commitment we’re passionate about. We’ve been working for over a year to create a more powerful solution to help clients protect their financial assets against attacks by cyber criminals. The policy focuses on the kinds of coverage that directly address the key fraud risks that businesses face – losses to their bank accounts through cybercrime. Cybercrime is a major concern for businesses, especially since they are typically liable if cyber criminals steal funds from their business accounts. They often don’t have the appropriate insurance in place and are finding it more difficult to protect themselves in this ever-evolving, increasingly sophisticated cybercrime environment.
KS: What does the coverage cost?
PG: Any business that has a deposit account at Grandpoint Bank or its divisions is automatically eligible to enroll in the policy and select from a range of coverages with premiums that start at $30 per month.
KS: Thank you James, Howard and Petra for taking the time to share your insight and expertise. For more information about the Client Cyber Crime Insurance coverage being offered by Grandpoint Bank you can visit their website: www.grandpointinsurance.com or call (661-702-6039) or email Howard Miller (HowardM@lbwinsurance.com).
What You Can Do Today
You can protect your business against unnecessary financial losses by following these risk management best practices:
- Encrypt sensitive data at rest, in transit and on mobile devices.
-
Provide employees responsible for wire transfers with anti-fraud training, including the detection of social engineering, phishing, spear phishing, or other confidence tricks.
-
Use e-mail authentication to ensure that e-mail received has originated from an authorized system (e.g. SPF-Sender Policy Framework; DKIM-Domain Keys Identified Mail).
-
Verify transfer requests and account detail changes using a method other than the initial contact method before acting on a transfer (e.g. the initial request is received by e-mail and verification is done by telephone).
-
Verify incoming checks by confirming funds are available before performing services or transferring any of the funds.
-
Change your passwords frequently.
-
Implement dual control for your bank accounts so that you always have a different person initiating a wire than the person approving a wire.
-
Set up alerts in your online banking profile to notify you of when payments are made.
-
Always call to verify when payment instructions change or you are setting up a new vendor or client.
About the Experts
James Melendres, Snell & Wilmer—Partner, Co-chair of Privacy, Data Protection, and Cybersecurity Practice
James Melendres is co-chair of the Cybersecurity, Data Protection, and Privacy practice and co-chair of the White Collar Defense and Investigations practice. He focuses on cybersecurity incident preparation and emergency response, related regulatory compliance and civil litigation as well as white collar criminal defense and government investigations. Prior to joining Snell & Wilmer, James served in the leadership offices at the Department of Justice as Counsel to the Assistant Attorney General where he oversaw legal and policy issues regarding sensitive cyber matters. He also led some of the Justice Department's most high-profile and complex matters, including the prosecution of former Central Intelligence Agency Director David Petraeus for mishandling classified information and making false statements to the Federal Bureau of Investigation.
Howard Miller, CRM, CIC, LBW Insurance and Financial Services — Vice President, Director of LBW’s Tech Secure® Division
Howard Miller brings over 20 years’ experience in property and casualty insurance. He specializes in insurance and risk solutions arising out of cyber security, cyber crime, intellectual property, and technology products and services. He is a founding member and leadership council member of the non-profit Secure the Village. In 2016 he was the first licensed agent to provide a cyber-crime insurance program for financial institution customers. He frequently delivers custom presentations on technology insurance and risk management topics for industry groups and executives.
Petra Griffith, Director of Product Development for Grandpoint Bank
Petra Griffith is the director of product development at Grandpoint Bank where she manages new product and business initiatives. Prior to joining Grandpoint, Petra was a senior product manager with Yahoo, where she led monetization products for Yahoo's media experience division. Previously, she helped start two start-ups in the Bay Area, iPrint.com and ZuluSports.com, and launched new products within larger fitness and media companies, including 24 Hour Fitness, BSkyB and Time, Inc.
Petra earned her undergraduate degree in International Politics and Economics, and German Cultural Studies from Middlebury College in Vermont, and an M.B.A. from the London Business School. You can follow Petra on Twitter (@petragriffith) and find her on LinkedIn at
www.linkedin.com/in/petragriffith.
ihttps://www.pwc.com/us/en/private-company-services/publications/assets/pwc-gyb-cybersecurity.pdf
iihttp://www.law360.com/articles/653008/employee-negligence-top-cause-of-data-breaches-report
iiihttps://www.biztimes.com/2016/03/28/bizinsights-park-bank-reduce-cyber-security-risks-with-employee-training/